10 common cyber security attacks and how to protect yourself from them
As cyber security attacks continue to rise, learning to protect yourself online is more important than ever! Especially because these attacks often lead to devastating consequences, including loss of important data and access to confidential information. Continue reading to learn all about the 10 most common cyber security attacks and how you can protect yourself from them.
- malware attack
- phishing attack
- man-in-the-middle attack
- drive by attack
- XXS attack
- watering hole attack
- password attack
- denial-of-service attack
- SQL injection attack
- brute-force attack
malware attack
A malware attack is also one of the most common types of cyber attacks. These occur when a user clicks a dangerous link or downloads an email attachment with malicious software viruses.
Several cyber security attacks you’ll learn about as you continue reading incorporate malware including, phishing, MITM, drive-by, and more.
malicious software
- Worm – Worms are standalone pieces of malicious software that can quickly spread throughout computer networks through constant replication. Worms rely on security flaws in the target system to gain access.
- Spyware – Spyware is software that allows attackers to steal sensitive information about a person without their knowledge. This is accomplished by monitoring and logging the victim’s device activity.
- Ransomware – Ransomware holds the victim’s system hostage until they pay money to the attacker. Ransomware can also be used to attack multiple people and deny access to several computers simultaneously.
- Trojan Horse – Trojans use malicious code to install software that seems legitimate but has hidden back doors into a system. This typically leads to the loss or theft of valuable data.
protection tips - Use antivirus software and firewalls to filter the traffic that may enter your device. Avoid clicking on suspicious links or attachments – especially from senders you don’t recognize. Also, make sure to regularly update your OS and browsers.
Phishing attacks are one of the most widespread types of cyber attacks. Phishing attacks are a form of social engineering where an attacker pretends to be a trusted and legitimate contact to gain sensitive information. This is accomplished by sending the victim a fake email that convinces them to download a malicious link or provide the attacker with their account credentials, such as passwords.
Most victims of phishing attacks are unaware that their private information was compromised. This allows attackers to easily reach other individuals they correspond with without suspicion.
whale-phishing
Whale-phishing is a tactic that attackers use to go after an organization's "big fish." These attacks are targeted at the company's employees with the most valuable information.
spear-phishing
Spear-phishing occurs when the attacker takes the time to research their target and then sends messages to them that they would expect to receive. This is often done through “email spoofing,” where the attacker fakes the “from” portion of the email. Hence, it appears to be from someone the victim knows personally. Because the messages appear legitimate, it can be tough to spot a spear-phishing attack.
phishing email example:
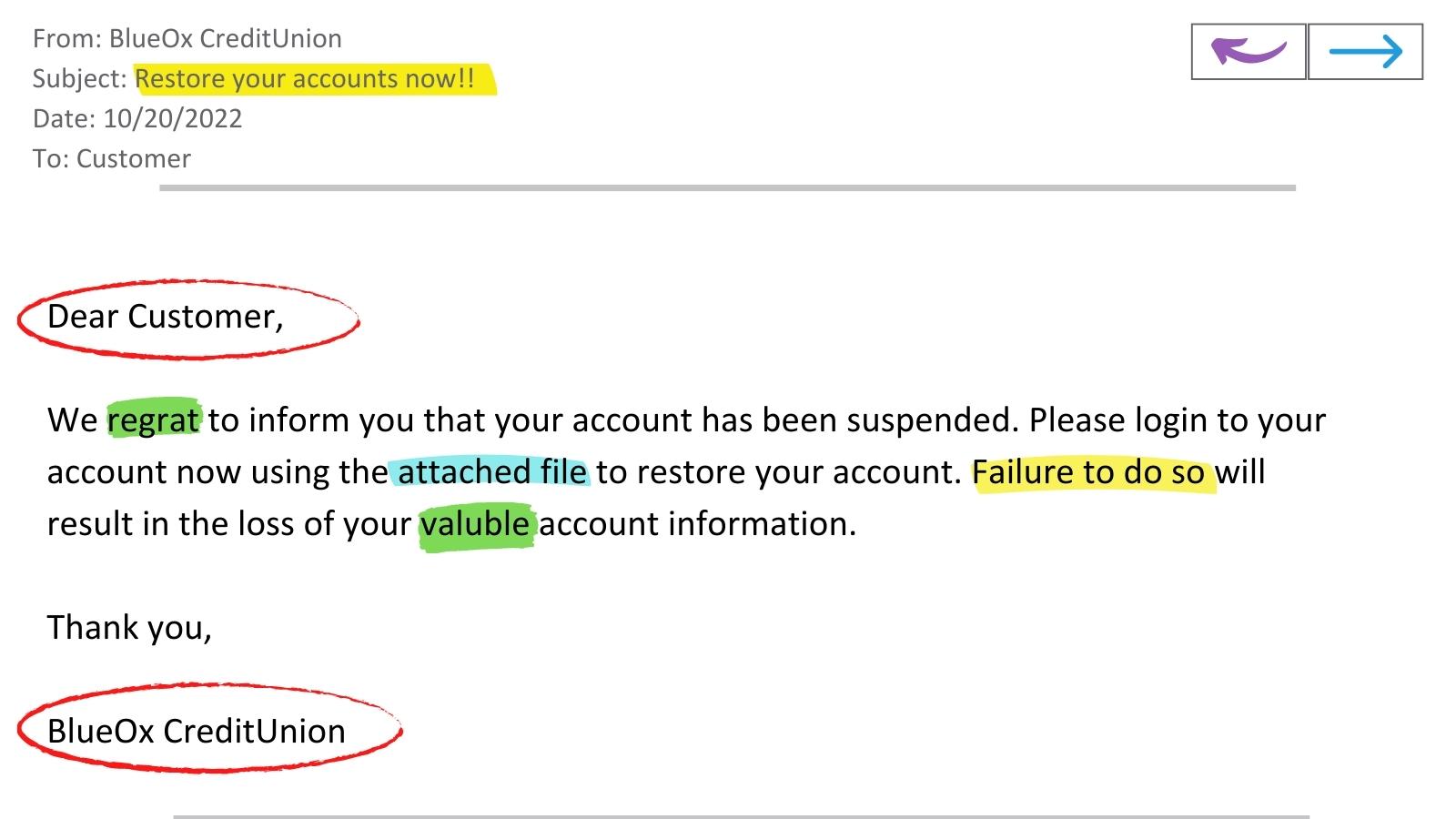
This is a common example of a phishing email. The highlighted text displays various hints that this is a scam email, such as:
-
- The subject line and last sentence of the email both display a sense of urgency.
- There are spelling errors throughout the email.
- The email is asking the receiver to download an attachment.
- The format of “customer” and “BlueOx CreditUnion” is inconsistent with how the company typically corresponds with its members.
protection tips – Pay close attention to the emails you receive. Reach out to the sender for verification before clicking any links or downloading attachments. Also, make sure to update your account information frequently
man-in-the-middle attack (MITM)
A man-in-the-middle attack is also known as an eavesdropping attack. This occurs when an attacker interferes with communication between two people, networks, or computers. As the name suggests, they position themselves between the two parties to spy on the interaction between them and gain confidential information.
Session hijacking is one form of a MITM attack. This occurs when an attacker takes over a session between a client and the server. This attack is effective because the attacker joins partway through the session, making the target believe they are still engaged in a trusted connection.
protection tips – Avoid using public Wi-Fi networks and use strong encryption on your devices.
drive-by attack
Drive-by attacks occur when the attacker embeds malicious code into an insecure website. The term drive by comes from the fact that if the victim simply visits the site, they’ll get infected. They aren’t required to click on a link or enter information like in other cyber attacks.
protection tips – Update your software often on all your devices, including your applications that could be used while browsing the internet. You can also download web-filtering software, which is used to detect if a site is unsafe.
XXS attack
With an XXS attack, the attacker transmits malicious scripts using clickable content and sends them to the victim’s browser. The script is inserted into applications the victim often uses, so they are viewed as legitimate. However, once the content is clicked, the script is executed, and the attacker can take over and act as the user.
One typical example is an attacker changing a transfer request from the victim’s Online Banking. The attacker will change the recipient of a transferred money request to themselves from the target's account.
protection tips – The easiest way to prevent this is to use a limited number of acceptable entries. Anything attempted after will be denied by the web application. There's also a technique called sanitizing, which checks to see if anything in the entered data could be harmful.
watering hole attack
Watering hole attacks occur when an attacker closely monitors a particular group of an organization and then infects the websites they frequently use with malware. Once the websites are infected, they also pass it on to the victim's systems. The attacker can then gain access to their personal information.
protection tips – Update your software and check for security patches regularly.
password attack
A password attack can be one of the most harmful for a target because they're the most frequently used access verification tool. There are many techniques that hackers can use to learn a person’s password. It could be as simple as finding it written down on the target’s desk to as complex as intercepting network transmissions and grabbing passwords that aren't encrypted.
Sometimes the attacker can even guess the password if it’s a default or something too simple. This can be accomplished through brute-force or dictionary attacks. A brute-force password hack uses basic information about the target, such as their name or birthdate. Dictionary attacks occur when they use common words or phrases to guess the password.
protection tips - Use effective passwords and keep them to yourself! Never share your password with someone, and avoid writing them down if you can. Instead, use a password-protected document to store your passwords. Effective passwords include both an upper and lower case letter, various numbers, and special characters. Don’t repeat your passwords or use the same password for different applications. Change your passwords frequently.
denial-of-service attack (DoS)
Denial-of-service attacks are specifically threatening to companies. These occur when an attacker targets systems or networks and overwhelm them with traffic. This results in the system's resources becoming drained to the point that the victim site can't provide services to those trying to use it.
One way they disrupt the system is by flooding it with illegitimate requests that the site attempts to respond to. This consumes all of its resources, so it can no longer function normally. These attacks often end with a complete shutdown of the target site. DoS attacks are commonly paid for by a business’s competitor hoping to benefit from their competition’s site crashing.
protection tips - Use firewalls that will detect whether a request for your site is legitimate. The fake requests will be thrown out, and your site can function as expected.
SQL injection attack
Also known as a Structured Query Language Injection, these attacks are a common way for hackers to take advantage of database-driven websites. The hacker injects malicious code into the target’s website search box. This could make the server reveal sensitive data or allow the attacker to modify/delete important information in the database. They can also get administrative rights through this tactic.
protection tips – Implement a validation process that keeps the user input more secure. Companies can also create a system within their structure that only allows departments access to information that their work directly depends on. The fewer people with login credentials to a network, the less likely an SQL injection attack will occur.
A brute-force attack is a simple method where the attacker tries to guess the login information of the target. This may seem time-consuming and ineffective; however, the attackers use bots to determine the credentials more easily. By providing the bot with a list of possible credentials, the bot will do all the work and try each one until they gain access.
protection tips - Use antivirus software and firewalls to filter the traffic that may enter your device. Avoid clicking on suspicious links or attachments – especially from senders you don’t recognize. Also, make sure to regularly update your OS and browsers.
For more information about common scams and tips for protecting yourself, check out our BlueOx blog: top 10 cyber security tips.
BlueOx member security
At BlueOx Credit Union, we take the security of your information seriously. As our valued member, we want to provide you with information and helpful tips that you can use to protect your personal information. Click the button below to learn more about how we provide security to our members.
« Return to "BlueOx Blog"

